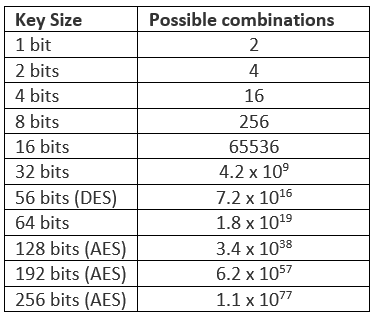
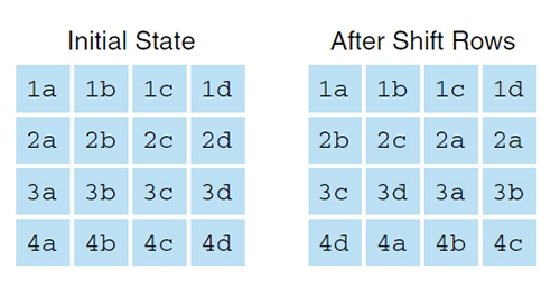
Amazon.com: The Design of Rijndael: AES - The Advanced Encryption Standard (Information Security and Cryptography) eBook: Daemen, Joan, Rijmen, Vincent: Kindle Store

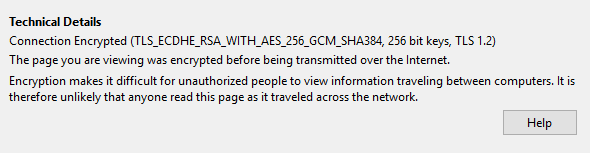
Aes encryption and hashing used for data security on amazon web services ijaerdv04i1067530ll by Editor IJAERD - issuu

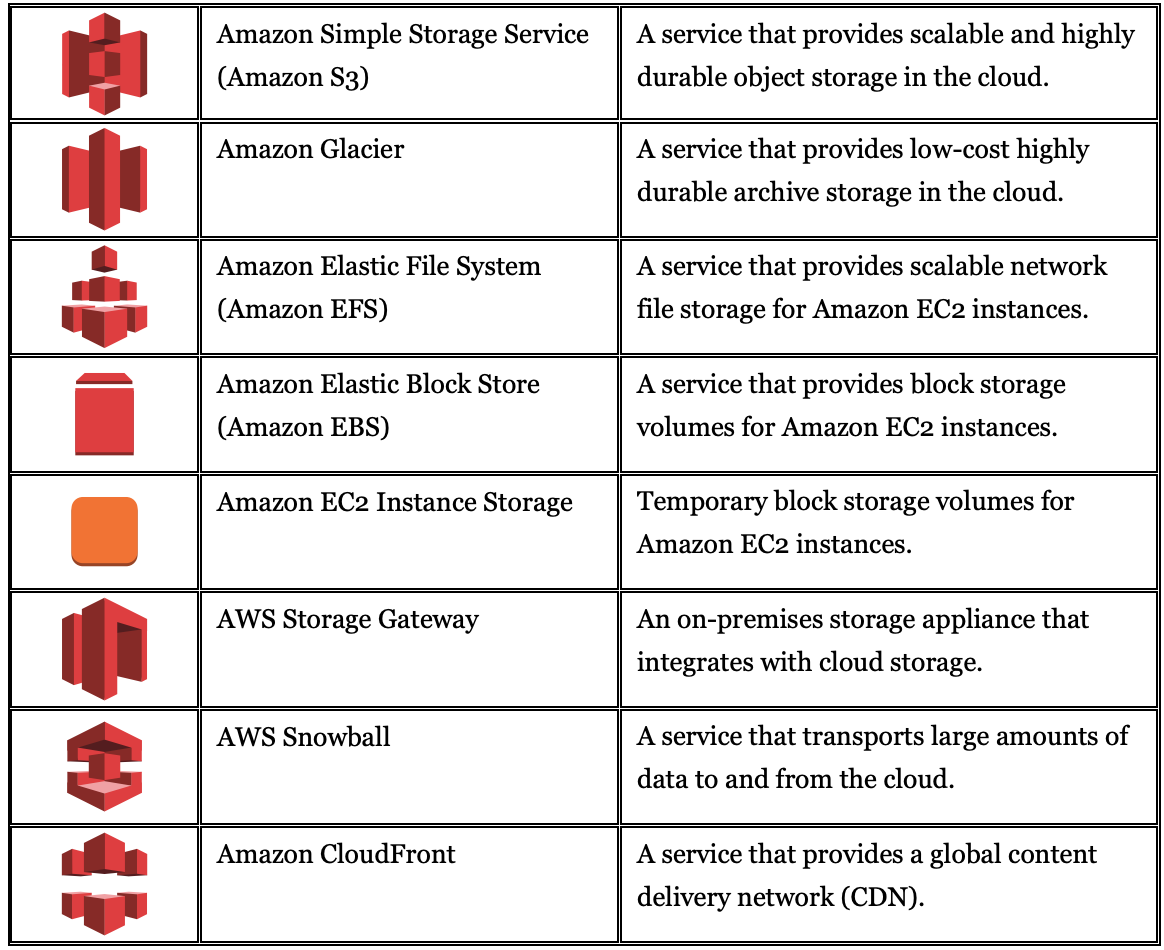
Client-Side Encryption and Decryption of Microsoft SQL Server Backups for Use with Amazon RDS | AWS Database Blog

Client-Side Encryption and Decryption of Microsoft SQL Server Backups for Use with Amazon RDS | AWS Database Blog

Amazon.com: The Design of Rijndael: The Advanced Encryption Standard (AES) (Information Security and Cryptography) eBook: Daemen, Joan, Rijmen, Vincent: Kindle Store