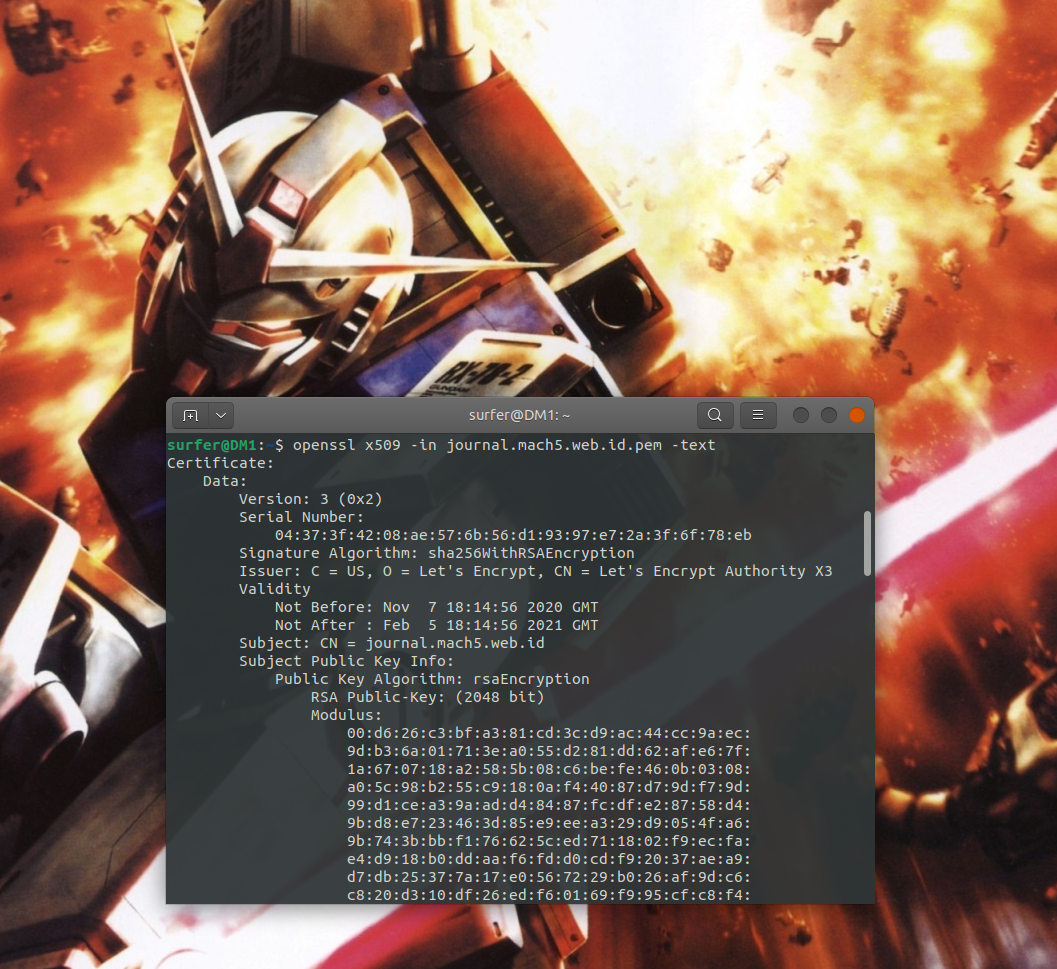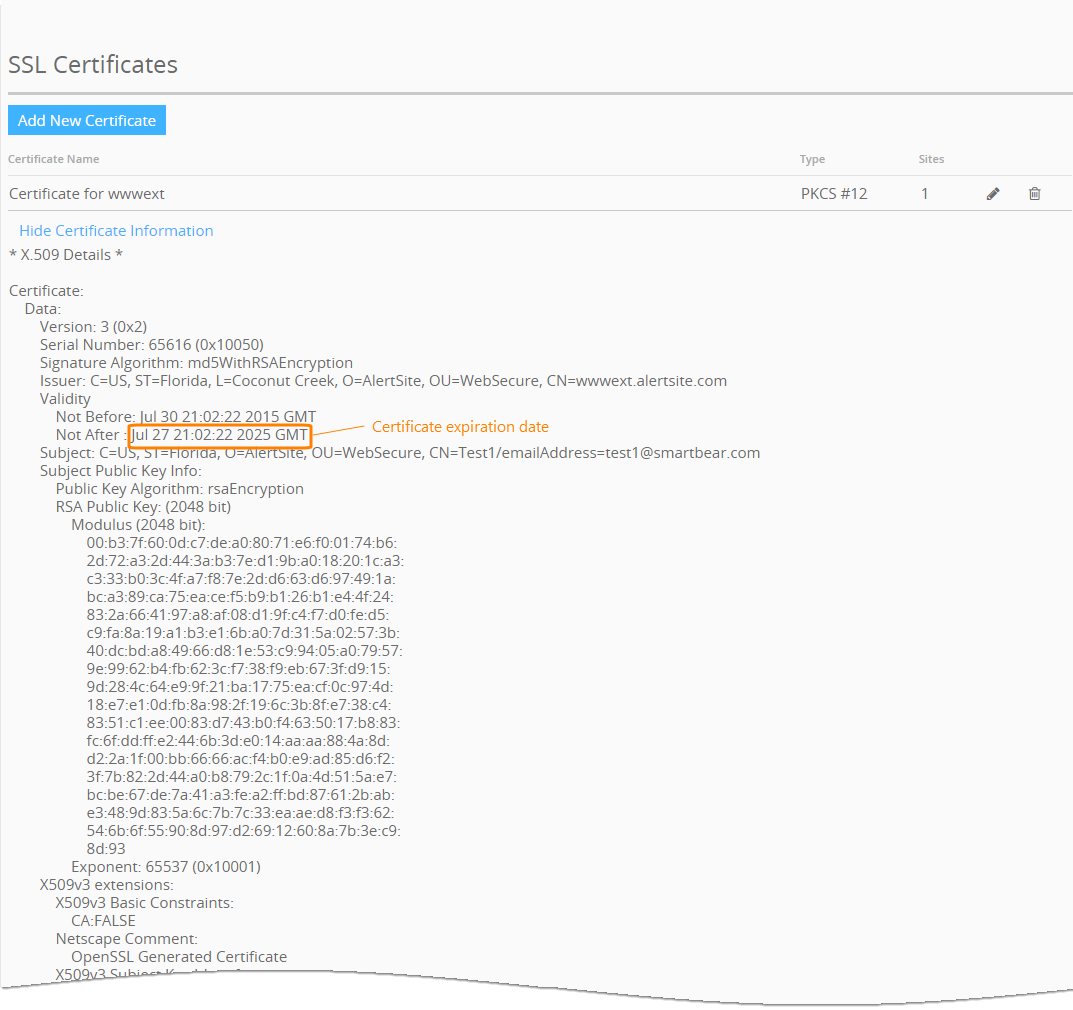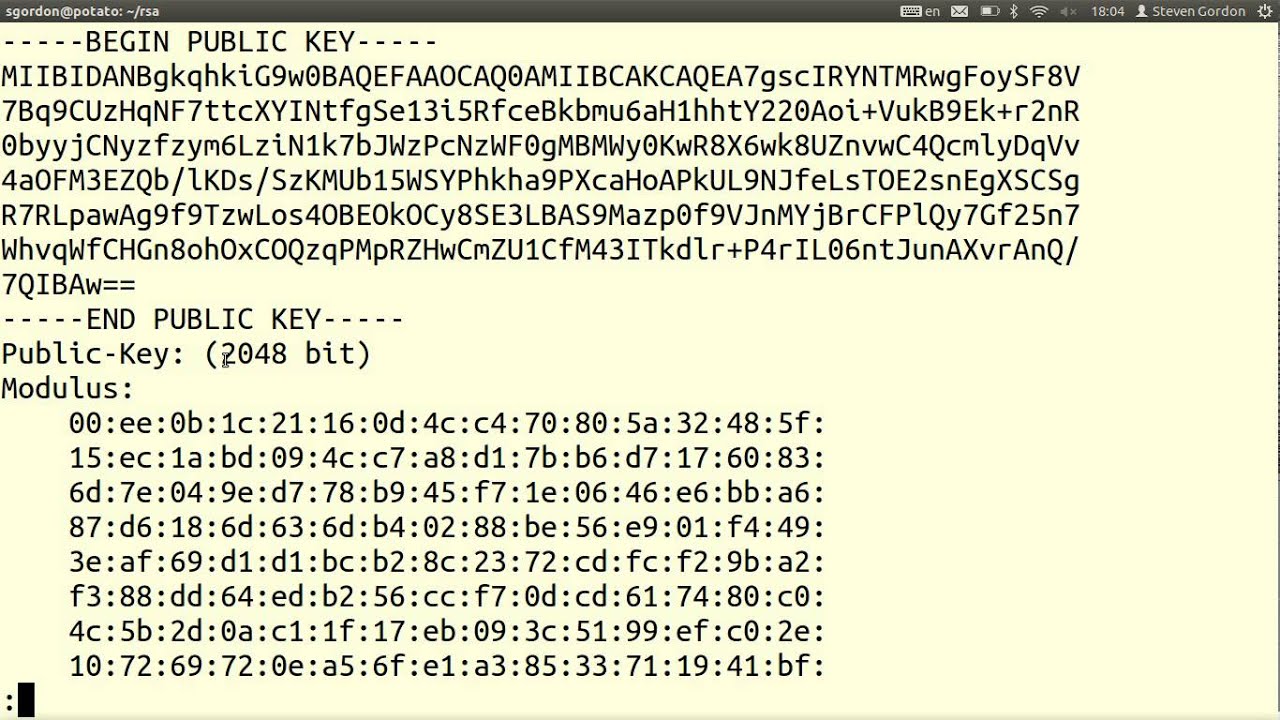
Anatomy of OpenSSH Key Revocation List (KRL) File | KEYPER: Manage SSH Key and Certificate Based Authentication
SHA-512 checksum summary Service and recovery pack FB14 Service pack.zip: de d8 12 31 cf 1f 0d c2 4f 4b 1e 8e c3 1a 43 47 52 a0
Wrong routing using OpenVPN connect - correct through OpenVPN community edition - OpenVPN Support Forum
10/3/2014 This presentation shows how to edit the default translation table source code that is provided in Sterling Connect:Dir